What are the human factors in a data breach, and how can they be remedied? DPAS Founder Nigel Gooding explains.
The human factors in a penalty shoot-out are much akin to a Data Breach.
The expectation of sports fans that a professional athlete should be able, in the final of a major competition, to perform a task with absolute precision because “it’s their job” is an expectation doomed to fail. In Football, the penalty shoot-out should be an easy task for a highly paid professional – despite being 19 years of age and played 120 mins of nerve-wracking gameplay.
Forget the physical and mental fatigue. They are practised, trained, and aware of what they need to do, despite being a human being. The fact that this goal could win or lose them a major trophy, in front of 60,000 fans, the world on TV, and they have one of the best penalty savers in front of them, is lost on many fans. They expect them to act like machines, switch it on, instant response and slot the ball home in the position of the laser-guided ball kicker.
Many years ago I owned a half-share in a racehorse. The horse went well on the gallops, but my fellow owner could not understand why the gallops form was not replicated when crowds, noise, and other distractions appeared on the racecourse. The horse is simply an animal and not a machine. Like the penalty takers, despite all the training, practice, and awareness, the conditions of training could never be replicated. Mistakes happen.
The next month we will see athletes who have trained for five years for their shot at an Olympic gold fall flat on their faces, despite being in the form of their life on the training ground.
How does this apply to a data breach?
The world of professional sports has similarities to the workplace. In particular, to the developing of strategies both pre- and post- Data Breach. The often-parroted response to many following a Data Breach is that “more awareness and training” is required if only they did what we employers asked and followed the training. This false premise ignores the fact that in a pressured workplace, you are unlikely to be able to replicate the training in a real-life event. The noise, the pressure to finish the task early to pick the kids up, or to please your boss, all contribute.
If we look at the published analysis, it is commonly accepted that humans can only focus on one task at a time. Most security systems and processes require more time. With employees focusing on getting their job done, security considerations are often secondary.[1]
Human Factors
Human behaviour is essentially goal driven. People perform tasks to achieve goals, at work: ‘I want to get this quotation to our customer today’. Or, in their personal life: ‘I want to get the best utility deal for us’. Employees are performance-driven and will do anything to get the job done, often ignoring all the training and the systems to find a workaround to deliver on this primary goal. They have what Beautement et al. called a Compliance Budget [2].
As the day progresses and enabling tasks to add up, the likelihood that they will seem too much and be bypassed increases. Furnell & Thompson coined the term security fatigue [3].
This challenge for practitioners was nicely summed up by the Cybok report into Human Factors on cyber breaches which said:
Even in conscious mode, people try to be efficient, resorting to ‘the closest thing they know’, that is, they are most likely to choose behaviours they use frequently or those that seem most similar to the situation they encounter. [4]
Data Breach: Root Cause Analysis
Therefore, like the racehorse, the athlete or the soccer player lining up to take the penalty kick, we are all human. Despite all the training, we still may fail to spot that one “phishing email” in our inbox of 300 daily emails. So what are we to do as practitioners to reduce the human factors in data incidents?
We have been engaged by clients to undertake “root cause analysis” of Data Breaches. With our extensive database of breaches, we have been able to identify causation and remedies, but also develop tangible measures such as cost and time. It will be no surprise to learn that people and process top trumps technology when it comes to Data Breaches, for all the reasons outlined above.
We found similarities between our findings and that of John Reason in his work of 2008, The human contribution: unsafe acts, accidents and heroic recoveries, which identifies four types of latent failures that are more likely to cause people to make errors [5].
- Individual factors such as fatigue but also inexperience and a risk-taking attitude.
- Human Factors include the limitations of memory but also common habits and widely shared assumptions.
- Task factors such as time pressure, high workload and multiple tasks. Monotony and boredom are equally error-inducing because people shift their attention to diversions. Uncertainty about roles, responsibilities and rules also leads to incorrect choices.
- Work environment, noise, interruptions and poor equipment and information. People are also particularly prone to error when rules and procedures change.
Remedies
So what remedies are we advising clients on at the moment to reduce the burden of Data Breaches?
- No blame culture and a reporting process that supports solutions developed as a team. Do not demonise those who make mistakes.
- Developing data flow accountability and ownership within the business, and linking back to corporate strategy.
- Fitting the data security processes to the people, not the people to the process, reworking if necessary.
- Putting those developing security solutions closer to the action so they understand the pressures of front-line staff.
- Building in Data Protection to the process, and eliminating manual intervention and repetition to the security process.
- Facilitating cultural change by embedding security and replacing existing behaviours in the workplace.
- Introducing networks of Data Champions at all levels to support and facilitate that change.
- Applying performative data to incidents including time and cost to produce tangible benefits and performance rewards.
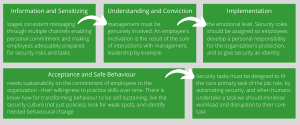
In simplistic terms, our approach to developing the Data incident maturity journey can be summed in this slide – click the image to enlarge.
Data security cannot be focused on transactional and automated tasks. However, we can make things easier for our staff who face the penalty kick, the tee off, first service or the starter’s pistol every single day.
Please feel free to contact us for more information on our Data Incident root cause analysis service or a Data Protection Audit. We would be happy to support your data breach cultural change.
If you would like to see this in practice, we have an article covering a recent case study, showing how a root cause analysis had helped our client. You can also learn the principles of determining the origins of such incidents by attending our Data Breach Root Cause Analysis training course.
References
[1] C. Herley, “More is not the answer,” IEEE Security & Privacy, vol. 12, no. 1, pp. 14–19, 2014
[2] A. Beautement, M. A. Sasse, and M. Wonham, “The compliance budget: managing security behaviour in organisations,” in Proceedings of the 2008 New Security Paradigms Workshop. ACM, 2009, pp. 47– 58.
[3] C. Herley, “More is not the answer,” IEEE Security & Privacy, vol. 12, no. 1, pp. 14–19, 2014.
[4] Cybok.org. 2021. Human Factors in Breaches. [online] Available at: <https://www.cybok.org/media/downloads/Human_Factors_issue_1.0.pdf> [Accessed 12 July 2021].
[5] J. Reason, The human contribution: unsafe acts, accidents and heroic recoveries. CRC Press, 2008.
by Nigel Gooding, LLM (Information Rights Law & Practice)
Nigel is founder of the Data Privacy Advisory Service, and he plays a vital part in our success. Due to his extensive experience, Nigel is recognised as a leading expert in the industry.