Common online scams and how to avoid them
We have all heard a story, or seen the documentaries, of people being scammed out of thousands of pounds by shameless scam artists. “Artists” seems too friendly… they are cyber criminals, a more fitting and accurate title. I am sure you have all had a moment of thinking, “but how?”, wondering how people could be so foolish. But do you really know how to spot scams, or how to make yourself a harder target?
One of the most outlandish and well-publicised scams was broadcast all over the world on Netflix in 2022: The Tinder Swindler. Most of us will have also heard about the ‘Nigerian Prince’. The majority of people I know have received a ‘HMRC Tax Refund’ email, or the more recent WhatsApp messages, where an individual claims to be a family member in need and asks for money. At first glance, it’s easy to see the financial incentive here. But the thing that links them all, however big or small, is data. Your data.
Generations respond to scams in different ways
We live in an era where sharing our day-to-day lives has become the ‘norm’. Facebook, Instagram, X, and even LinkedIn have become daily diaries, and include increasingly more personal details about our day-to-day lives. Back in 2017, the Economist wrote ‘the world’s most valuable asset is no longer oil, but data’. Yet here we are, happily sharing it for free, more than ever.
It’s a strange paradigm working in data protection, and being of a generation that was amongst the first to embrace social media. MySpace was a key part of my teenage years. However — and perhaps it’s because of my job — I am conscious of what I share, what I click on, the web pages I visit, and who has access to all of that information. But on either side of me are different generations with different outlooks, which potentially leave them more vulnerable to cyber criminals. My parents, grandparents, and older relatives perhaps have a naiveness to ‘the world wide web’, how emails work, and the potential risks associated with them that I spend my daily life talking about. They are forced to adapt to a world that is quite different to their ‘norm’, and at the same time, are expected to understand the do’s and don’ts. Don’t click on the dodgy attachment. Don’t give the man on the phone your bank details, even if it appears it’s the bank calling. Where are they expected to learn any of that information… without searching the internet?
Contrastingly, the younger generation live and breathe technology. Their daily lives are reliant on the Internet of Things. The culture is to share, to post, to like, and to comment. Yet, there is still very little education surrounding online safety and how to protect yourself from the nefarious individuals that are lurking.

Keeping ourselves safe
There are parts of protecting ourselves that are ingrained in society, and have been for decades. Don’t walk through the dark park alone at night, lock up your houses, make sure you don’t leave your car windows open… Everyone habitually protects themselves from the kinds of opportunists you may be unfortunate enough to physically encounter. But there is huge disparity between how we protect ourselves from physical risk, and how we protect ourselves from virtual risk.
So, what do we do about it? I don’t know the perfect answer to that, but I do know that the only way we are going to be able to progress is through education. Making the general public more aware of the risks, what to look out for, and how to react. This needs to be done in an accessible way, allowing the most vulnerable people in society to have access to information that is arguably most necessary for them.
How to avoid becoming a victim
There seems to be some irony here, writing a blog that is destined to be only accessible online… about online safety… whilst preaching that the only information available is online. However, here we are. So, if this reaches you, at least try to relay the information to someone it wouldn’t reach otherwise. We have all got a part to play.
If you’ve made it this far, great! Time for the bit that’s actually useful, the stuff you need to be aware of, and how you can make sure you are protecting yourself as best you can. I am going to focus on ‘phishing’, as there just isn’t enough time to cover everything, and it is, after all, one of the most common tactics employed to con unsuspecting victims in a variety of ways…
UK Phishing Scams
First up, what even is phishing? Phishing falls under the umbrella of ‘social engineering’. Social engineering is a broad term that refers to the psychological manipulation of individuals into performing actions or divulging confidential information. Unlike technical hacking methods that exploit software vulnerabilities, social engineering exploits human vulnerabilities like trust, fear, curiosity, or ignorance.
Social engineering attacks are often designed to appear as legitimate interactions, convincing victims to bypass normal security protocols. The attacker might pretend to be a trustworthy figure, such as a coworker, IT support, or a family member to persuade the target to share sensitive information, click on malicious links, or grant access to restricted technology.
Phishing is one of the most widespread forms of social engineering. Attackers send deceptive emails, text messages, or website links that are designed to look like legitimate ones (such as banks, online services, or government agencies) to trick victims into revealing personal information like passwords, credit card numbers, or Social Security numbers.
If you are sitting here thinking that you have never received a phishing email/message, I would bet my bottom dollar that you have, and you just didn’t know it. As of June 2024, the National Cyber Security Centre (NCSC) have received over 32 million reports of phishing. There are numerous common types of attacks in the UK that have been doing the rounds for a while now…
HMRC Tax Refund Scams
This one will usually look something like this…
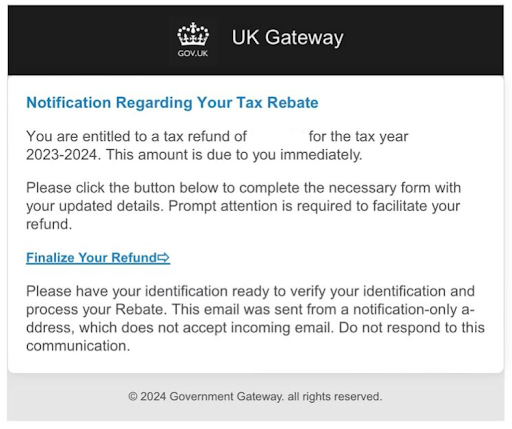
Potential victims receive emails that are designed to look like a HMRC notification. The email will say you are entitled to a tax refund, and ask you to follow a link to claim.
There are a couple of red flags here. My first piece of advice is DO NOT CLICK RANDOM LINKS. Even if you think it could be legitimate, go to Google and find the webpage through an organic search. Do not follow links if you have any doubt about the authenticity of the email/message. If you are really unsure, ring them on a number that you have researched yourself (so not the one that might be in the email). Speak to a real person.
HMRC have publicly announced that they will NEVER send a tax refund notification via text message, or email. So just keep checking those brown envelopes!
Delayed Parcel Scams
This example used Evri, but look out for Royal Mail ones too.
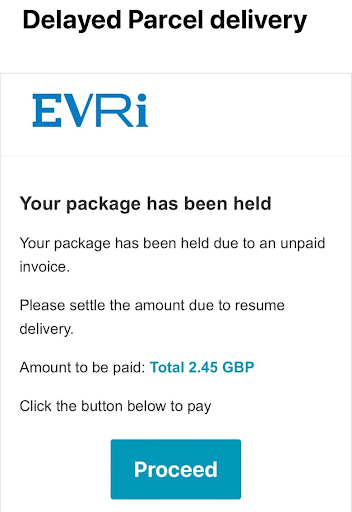
One of the most frequently reported scams is of this nature. Ultimately, the attacker is hoping you’ll click the link and make a payment to collect ‘your parcel’. However, by doing so, you have provided your bank information to God knows who, and they now have a copy of enough personal data to potentially continue to use your card details.
Fake Social Media Account Scams
The modern day Nigerian Prince. Have you had a private message from the partner of your dreams? A celebrity?
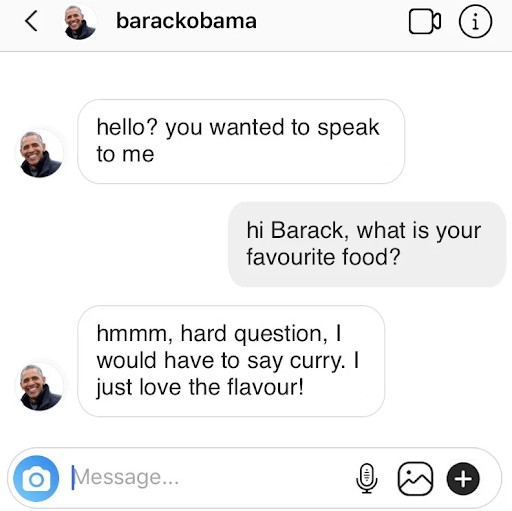
Sorry to be the bearer of bad news, but generally, if it seems too good to be true, it usually is. Often, these accounts can be spotted by viewing the whole account, and looking at how they interact with others. For example, we would expect Barack Obama to have a considerable amount of followers, and lots of engagement on previous posts. In contrast, fake accounts will usually have limited friends/followers, and very little engagement on posts.
Where ‘normal’ people are concerned — and by that, I mean not celebrities — check out their interactions with other people too. Do they have family and friends in photographs? Have they commented on each other’s posts? Also, be wary of accounts that have recently been created.
WhatsApp Scams
This one seems to be the rising star — a fraudulent message that appears to be from a family member. This is often followed by a request to send money to this ‘friend’…
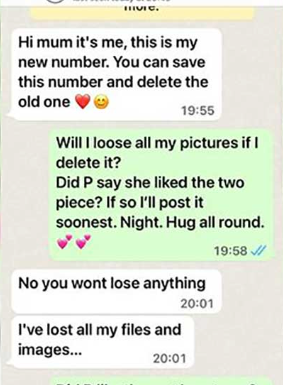
Unfortunately, this one is less about how to avoid receiving the messages, but more about being able to spot them. Of course, be conscious of where you share your phone number. But if you receive any unusual messages, always double-check any information. Try calling the number you already have for that person, and never send money or additional information.
You can stay on top of the latest scams here.
Spotting Fakes
So, now you have seen some examples of online scams. But what should you look out for? There are a few things to note that should set the alarm bells ringing. If you are ever suspicious, do not respond, and consider the following:
Authority
Is the message claiming to be from someone official, for example, your bank, doctor, a solicitor, or a government department? Criminals often pretend to be important people or organisations to trick you into doing what they want… remember that manipulation thing?
Urgency
Are you being told that you have a limited time to respond (such as ‘within 24 hours’ or ‘immediately’)? Criminals often threaten you with fines or other negative consequences if you don’t respond fast enough.
Emotion
Does the message make you panicky, fearful, hopeful, or curious? Criminals often use threatening language, make false claims of support, or tease you into wanting to find out more. Take a breather!
Scarcity
Is the message offering something in short supply, like concert tickets, money, or a cure for medical conditions? Fear of missing out on a good deal or opportunity can make you respond quicker, and this is what the attacker is hoping for.
Current events
Are you expecting to see a message like this? Criminals often exploit current news stories, big events or specific times of year (like tax reporting) to make their scam seem more relevant to you.
You can find some helpful resources from the NCSC here. This link also includes information on how to report suspicious communications.

How to best protect yourself and others
Recognising a scam is great, but being assured that you won’t fall victim to some of the nasty schemes is a bonus. But as Erasmus once said, prevention is better than cure. So, let’s look at some ways that you can prevent yourself from ending up in any of these situations, and how you can best protect yourself and others from falling victim to these attacks.
Privacy Settings
How many of you have never even looked at the privacy settings on social media? I would expect quite a few. Utilise them! Make your accounts only visible to known and trusted individuals. Facebook includes features such as allowing you to be unfindable unless you have mutual connections. These features are especially beneficial to activate on accounts belonging to vulnerable family and friends. There is specific advice for a variety of popular social media organisations available here.
Privacy Notices
You have all seen them, and mostly ignored them. But did you know that these notices include information about how a company will use your data, how long they keep it for, and if they share it with anyone else. READ THEM! Before you give away your personal data, sign up to accounts for free trials, or use your information to access discount codes. Check where that data is going. The point of these notices is to give you enough information so you can make an informed decision.
Password Management
I get it — everyone is tired of having to include 10 characters, uppercase letters, lowercase letters, number, a special character, etc., etc. But these features are designed to help you. The NCSC recommends using three random words, this way your password is difficult to ‘crack’, and easier for you to remember than a series of random characters. Read their guidance here. Avoid using common words and series of numbers, so no ‘password123’ or dates of birth. It is also advisable to have a different password for key accounts — email, banking, and social media.
Multi-Factor Authentication
Turning on multi-factor authentication (MFA) is one of the most effective ways to prevent cyber criminals accessing your data. When you set up MFA, you will be sent a pin code (or similar) to a trusted number/email address. You then need to enter that code to prove it’s really you. So even if somebody has your password, they wouldn’t receive the additional code.
There are alternatives to the MFA pin codes that provide the same security, such as face ID and fingerprint authentication — different providers will offer different setups.
Digital Footprint
Less obvious, but just as crucial, is the need to be aware of your digital footprint — the trail of information you leave behind with every post, photo, and status update. This isn’t just harmless fun; criminals can exploit this publicly accessible data to steal your identity or craft more convincing phishing scams. Here’s what you should keep in mind:
- Think twice about what you’re sharing and who can see it. Have you set your privacy options so that only those you trust can access your posts?
- Reflect on whether your followers/friends really need to know every detail, or if some information, though seemingly harmless, could be a goldmine for cybercriminals.
- Consider how your online presence is shaped not just by what you say, but by what others might be saying about you, and what you interact with.
In a world where oversharing has become second nature, it’s easy to overlook the risks. But by being mindful of what you put out there, you can make yourself a harder target for those lurking in the shadows of the internet.
Useful Resources
There are a plethora of resources available, and the NCSC publishes a huge amount of educational material that is intelligible and easily implemented by everyone — so you don’t have to be into tech.
Check out the NCSC’s list of useful guidance.
There are also lots of ‘fun’ resources available that might help you translate some of the information to friends and family.
For example, on www.HaveIBeenPwned.com, you can check if your email address or phone number have appeared in a data breach.
Which? also has a dedicated webpage on recent scams here.
You can also test your ability to spot phishing emails here.
Social media and children
Most social media accounts require users to be at least 13 years old. However, it is easy to sign up with a false date of birth. For expert advice about how to keep children safe online, please refer to:
- Thinkuknow: National Crime Agency: education programme for children
- Internet Matters.Org: Social Media Tips
- NSPCC: keep your child safe on social network
So, there we have it: a whistle stop tour. There is an insurmountable amount of discussion points here. We would be here all day if we tried to cover them all, and with the addition of artificial intelligence (AI) into the mix, it only adds to the complexity (NCSC have made a post about that too if you’re interested). But the key here is we all have a part to play, so next time you pop to your grandparents’ for a cuppa, check their security/privacy settings and talk to them about what to be careful of. When your young relatives want to post that funny video on Facebook, remember the potential consequences. And next time somebody wants your data for free, just remember, it’s more valuable than oil!

How DPAS can help
If you are a business struggling with information security knowledge, or unsure of how to educate your workforce on online security, get in touch with the DPAS team. Our experienced and dedicated professionals can provide a variety of services or training courses to get your organisation to where it needs to be.
Click here to view the services we offer, or here to explore our list of training courses.
Engage. Educate. Empower.